Crabby's Credential Stuffing: Australian Account Takeovers in 2024
Abstract
In January 2024, breaking headlines were made by national Australian news agencies that 50+ major Australian brands such as Officeworks, The Iconic, and Dan Murphy’s had customer accounts compromised through credential stuffing attacks. Victim customers reported stolen funds and credit card fraud.
This research concluded that compromised Australian accounts were first advertised for sale in July 2023 using public Telegram channels by a threat actor called “Based”. Account sales were transacted on Discord, and two websites, before the cyber-crime business was acquired in November 2023 by an infamous international account vendor called “Juicy”. This vendor rapidly rose to popularity in past year by acquiring many other well-known account shops. The Australian account shop was rebranded as “Crabby” and has utilised three websites and multiple Telegram channels to sell compromised AU accounts, which has continued to this day.
Low-level fraudsters purchasing the stolen accounts were observed to demonstrate poor operational security, often oversharing information related to their identities and the crimes they were committing. This included order reference numbers, recorded videos, and plans to collect fraudulently purchased goods including the time and store location. Whilst they are motivated by financial gain, it is clear they are also driven by the excitement and challenge of engaging in illicit activities, and would take risks in pursuit of their goals.
This scenario presents a challenge for law enforcement who wish to disrupt this activity, due to compromised account vendors operating out of foreign jurisdictions. The key to disrupting the rise of this crime lies in targeting the demand side of the equation. By focusing on catching and prosecuting the low-level fraudsters in Australia who are buying the compromised accounts, law enforcement can set a precedent and deter others from engaging in similar activities.
Detailed Research
1. Breaking news in 2024
In the beginning of 2024, news headlines highlighted that thousands of Australian customers experienced their online accounts being compromised and used for fraudulent transactions. It affected customers of many well known brands, such as Dan Murphy’s, The Iconic, and Officeworks, to name a few. This caught the attention of the Prime Minister, who shared the following statement in January 2024:

“This is a scourge and there are so many vulnerable people being ripped off who’ve acted in absolutely good faith and we need to make sure they are protected.” Anthony Albanese, Prime Minister of Australia
Further reading:
- Dan Murphy’s: Credential Stuffing FAQ
- The Iconic: Suspected Unauthorised Access
- 7 News: Thousands of Aussie shoppers victim to new major hack impacting brands including Dan Murphy’s, Binge and TVSN customers
- The Sydney Morning Herald: Thousands of Australians hacked in credential stuffing credit card scam
- Yahoo News Australia: Major brands hit by credit card hack
- ABC News: The Iconic isn’t the only one saving your payment details.
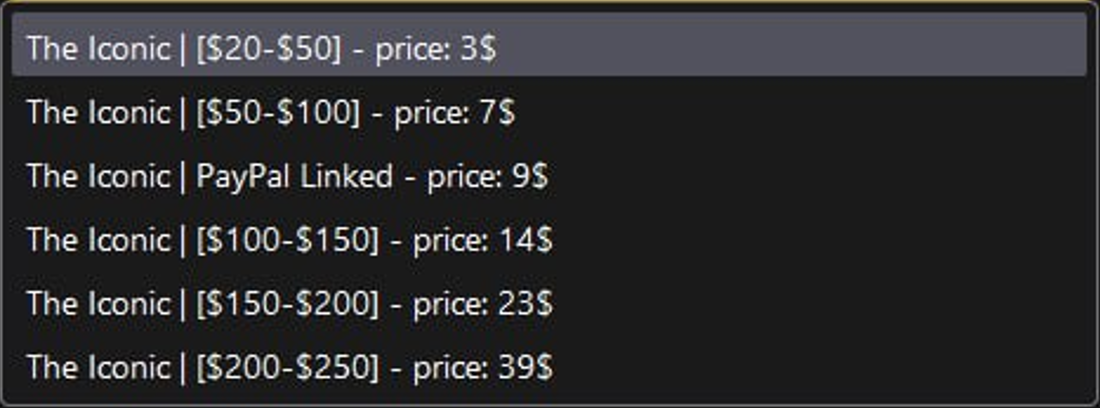
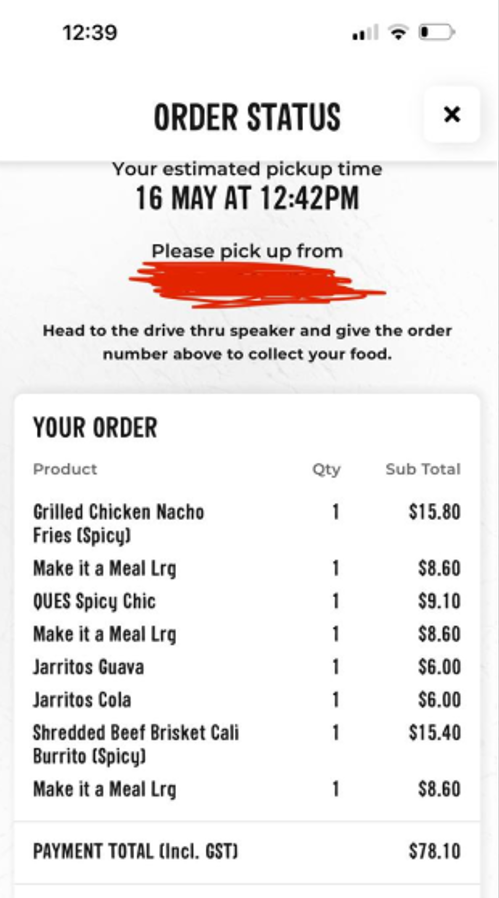
The hijacked accounts are used for fraudulent transactions, with the primary intention of revenue generation. Retail products with a high resale value such as phones, laptops, gift cards, headphones, watches and more were being fraudulently purchased. Here are some examples of the orders fraudulently submitted and collected by low-level fraudsters, based on images they have shared in Telegram chat rooms:
Officeworks
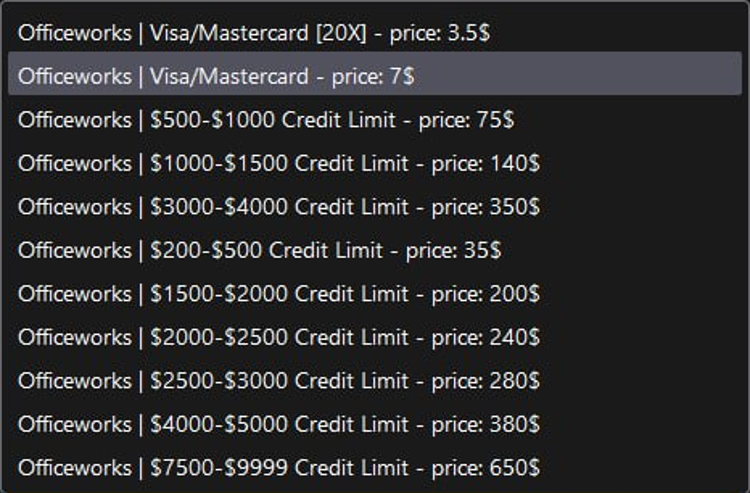



The Iconic

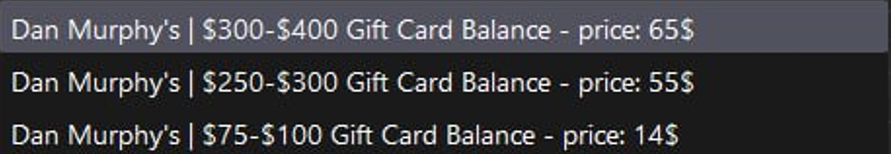
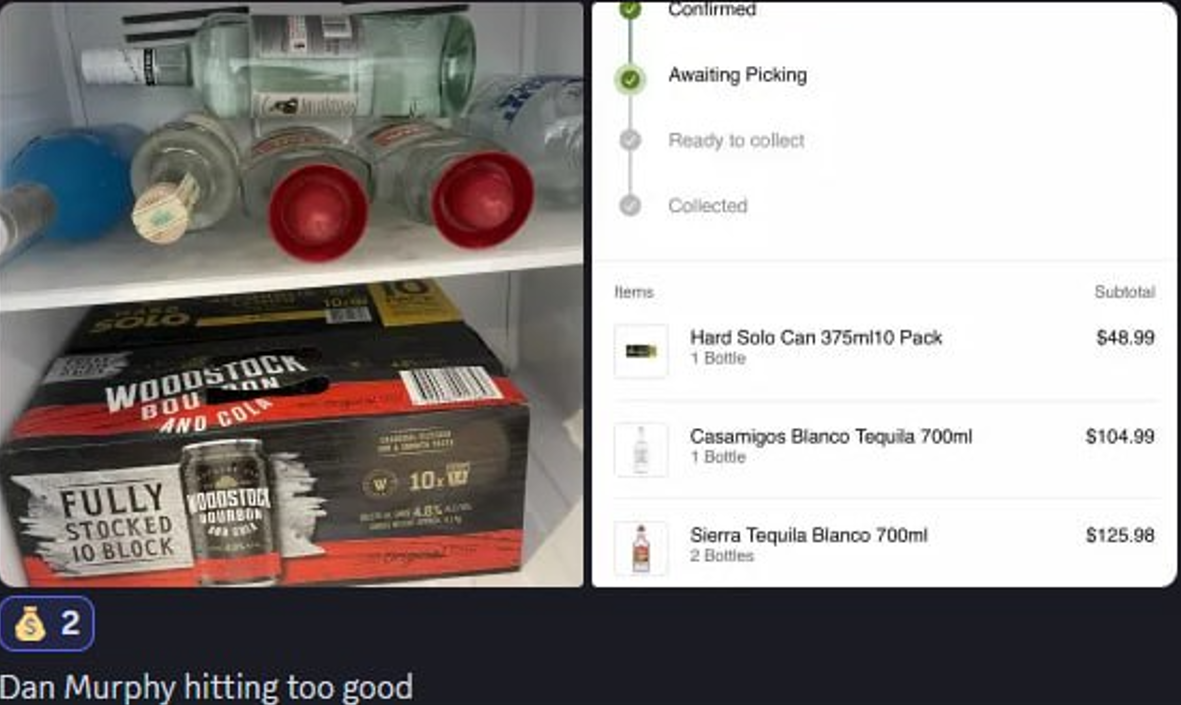
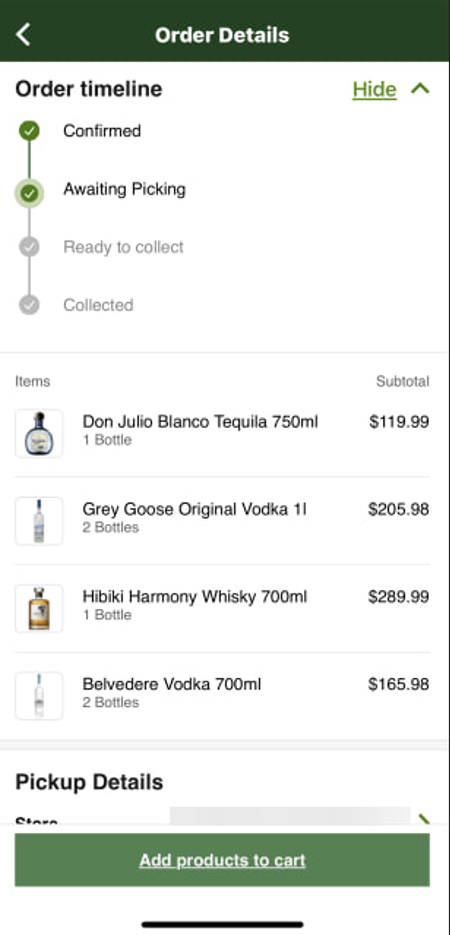
Dan Murphy’s
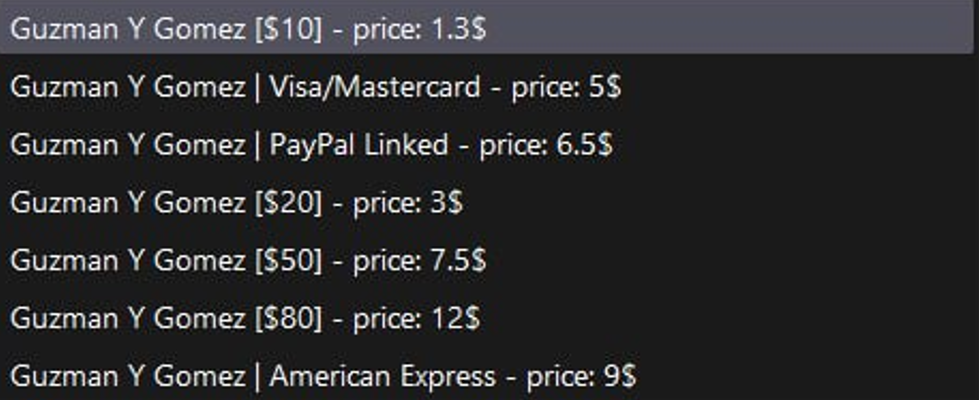
Guzman Y Gomez

2. What is credential stuffing?
Customer accounts are compromised through a “credential stuffing” attack. This attack is where a threat actors tries to authenticate to target websites using email and password combinations, or credentials, from unrelated third party data breaches.
The success of achieving unauthorised access to a victim’s account in a credential stuffing attack, primarily relies on customers using the same password for multiple services, or a similar permutation of a password that has been historically compromised. This means, that once one of their online accounts has been compromised, with a email and password combination being leaked, all of their other accounts are now susceptible to unauthorised access via a credential stuffing attack.
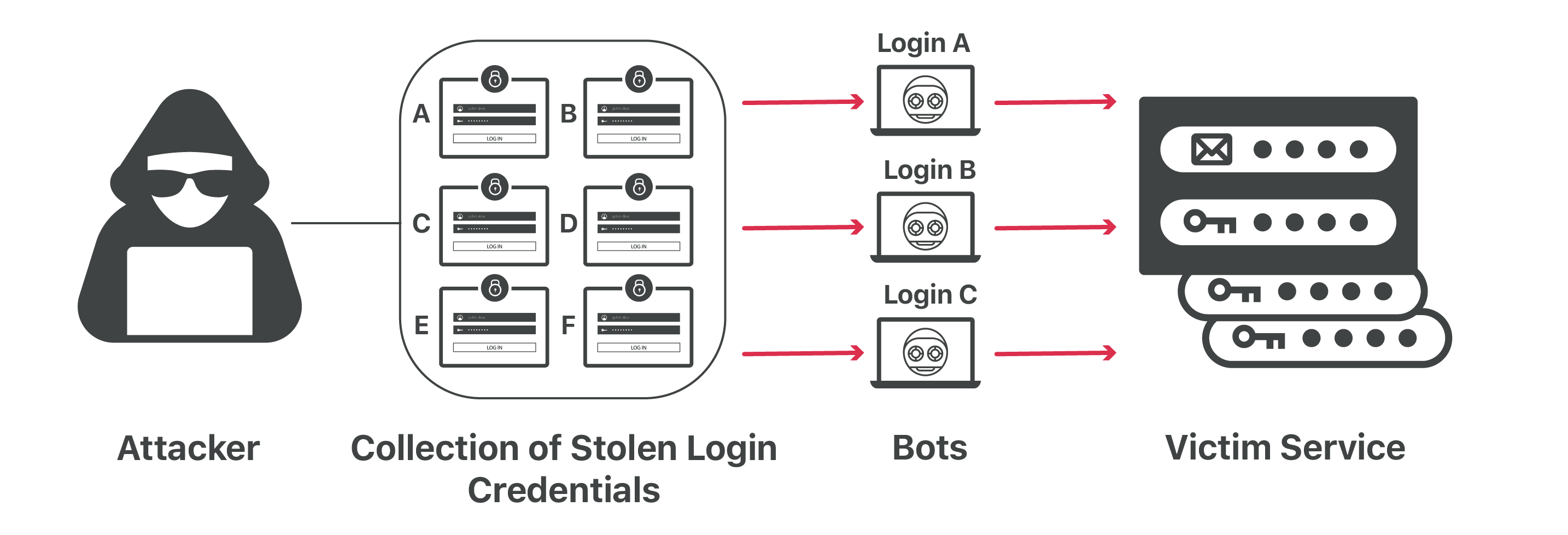
Credential stuffing attacks are also referred to as “cracking” in underground markets. To perform cracking, multiple components are required including a cracking tool/script for automating the login process and scraping account information, residential proxies to rotate and bypass IP-based restrictions, and finally “combo lists” which are a combined list of usernames/emails and passwords for the tool to automatically attempt authentication to target websites, created based on historical data breaches.
3. Types of threat actors involved
Before proceeding, it’s important to distinguish the two different types of threat actors involved:
- Vendors are performing the credential stuffing attacks to identify valid username and password combinations to gain access to victim accounts. They sell the accounts to customers in bulk for financial gain.
- Customers are buying the compromised accounts from the vendors and are typically low-level fraudsters who need “boots on the ground” to reap any financial gain. They use the accounts to commit fraud, laundering stolen funds, or purchasing high value goods from retailers to collect and re-sell for profit.
4. Who is selling the compromised accounts?
Started with “Based”
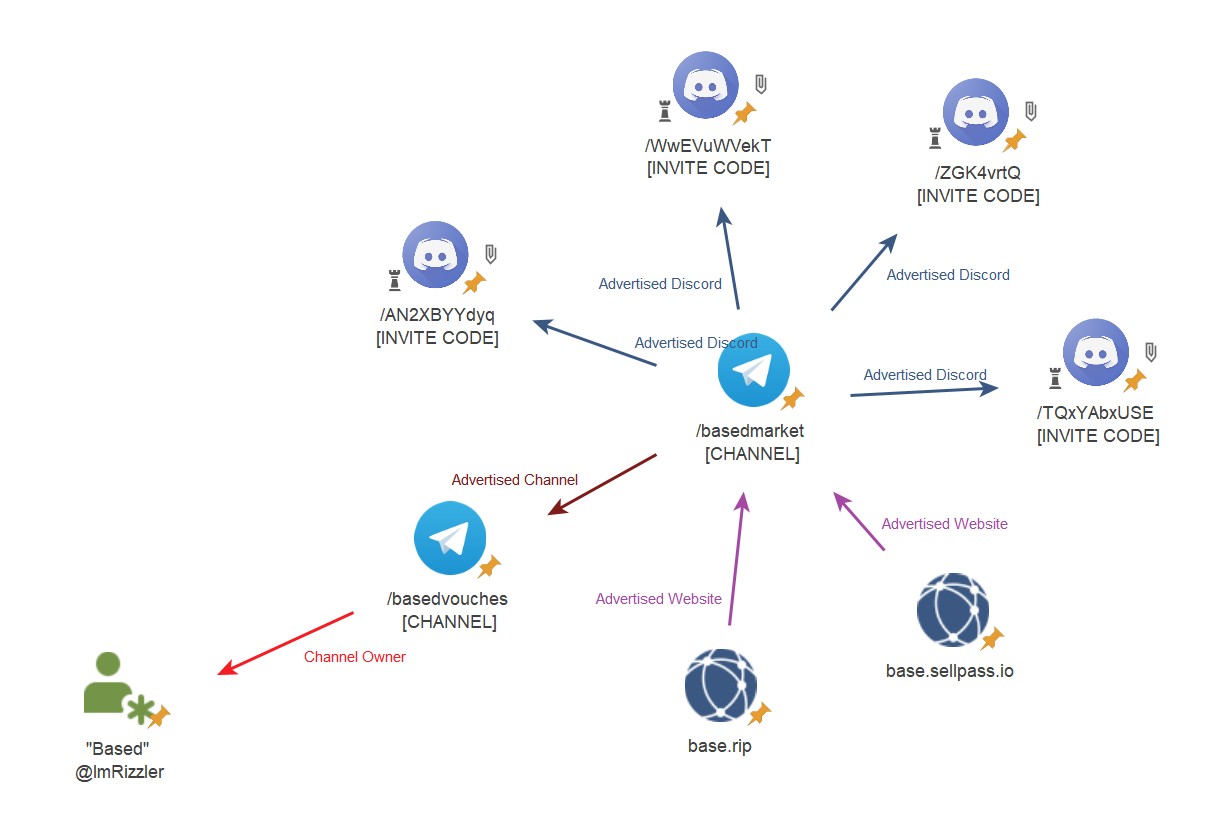
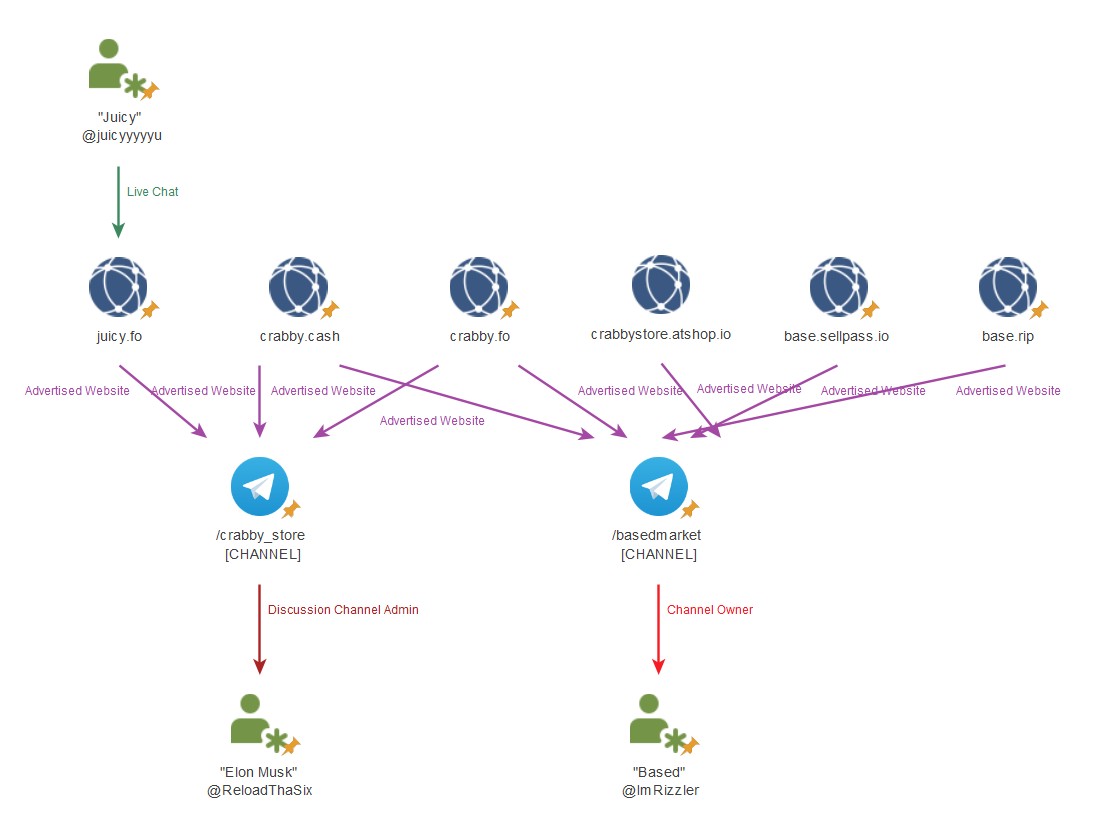
Compromised Australian accounts appeared online as early as 31 July 2023 by a user known as “Based” (@ImRizzler). The accounts were sold via a Discord channel, and also two websites (base[.]sellpass[.]io and base[.]rip). The primary Telegram channel for advertising was /basedmarket and vouches were kept on /basedvouches. Archived Telegram Channel Reference
Became “Crabby”
On 25 November 2023, “Based” sold his Australian account shop to “Juicy”, and the new shop was rebranded as “Crabby”. The telegram channel /crabby_store was used for advertising, and the website launched to sell the accounts was crabby[.]atshop[.]io.
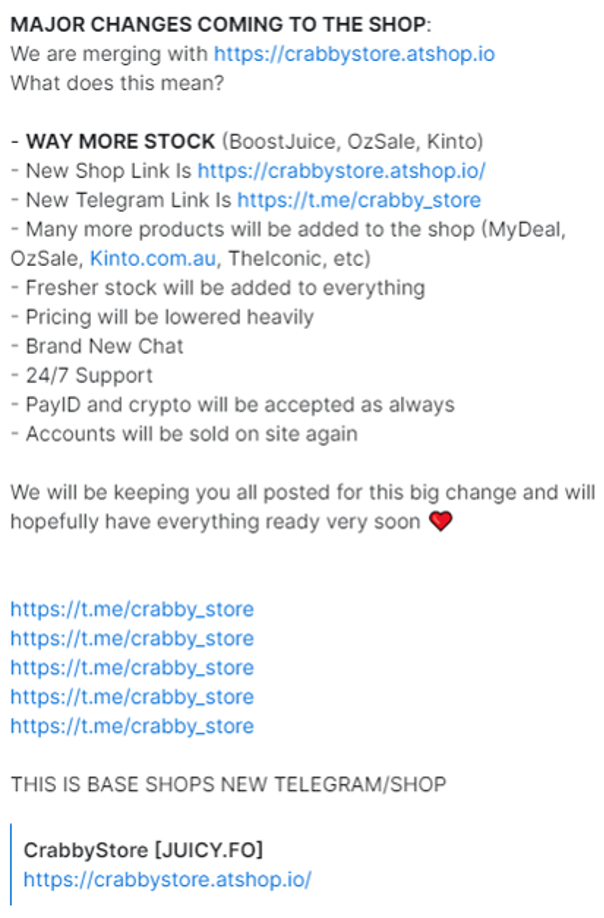

At the same time, a website redirect was setup for base[.]rip to forward traffic to crabby[.]atshop[.]io, and the base[.]sellpass[.]io shop had included a link to the /crabby_store telegram channel.
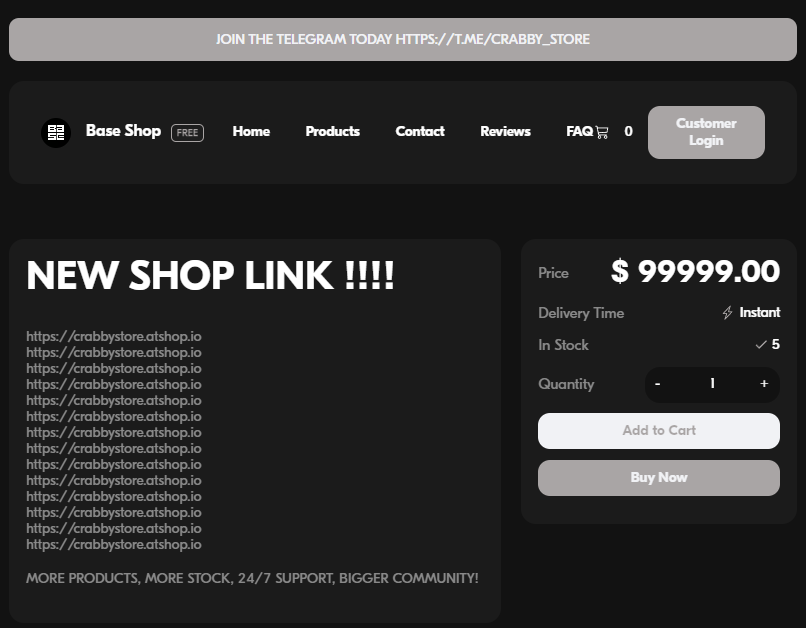
On 9 January 2024, the new owners changed the domain from crabby[.]atshop[.]io to crabby[.]fo, matching the same TLD as their main site juicy[.]fo. However, the domain was terminated by the registrar on 31 January 2024, and thus the website was updated again on 1 February 2024 to crabby[.]cash.
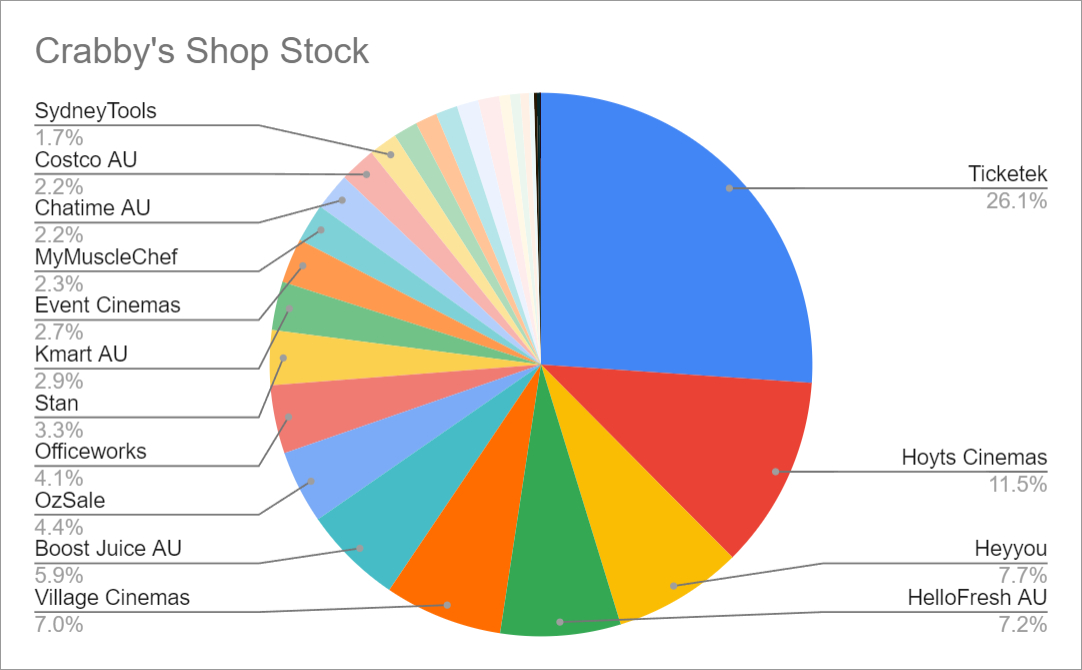
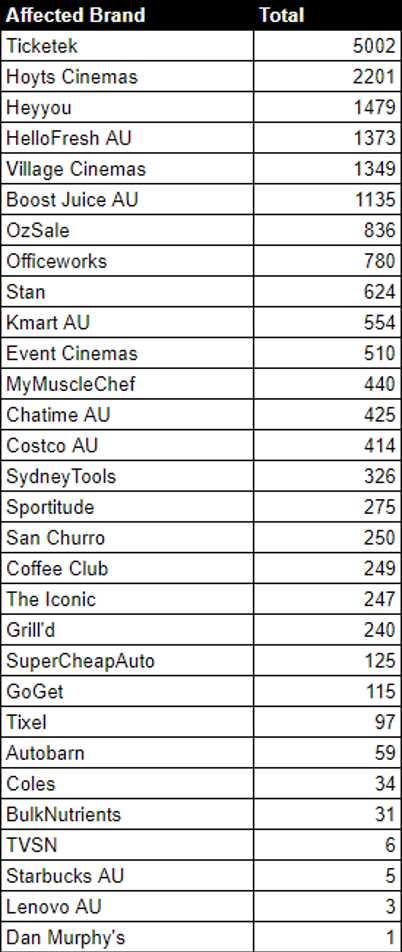
The crabby[.]cash website is still alive today selling compromised Australian accounts. As of 8 May 2024, a total of 19,185 accounts are for sale affecting the following brands.
Owned by “Juicy”
“Juicy” is an compromised account seller website for primarily USA, CA and UK based brands. Historically the website sold AUS compromised accounts, but that is no longer the case since the launch of “Crabby”.

The juicy[.]fo website and telegram channels are maintained by one owner called “Juicy” @juicyyyyyu and three administrators called “Venchu” @Gvenchi, “TOXIC” @Toxlc001 and “Bobby” @bobby2x. “Juicy” and “Venchu” are also operator of the website’s live chat for customer support.
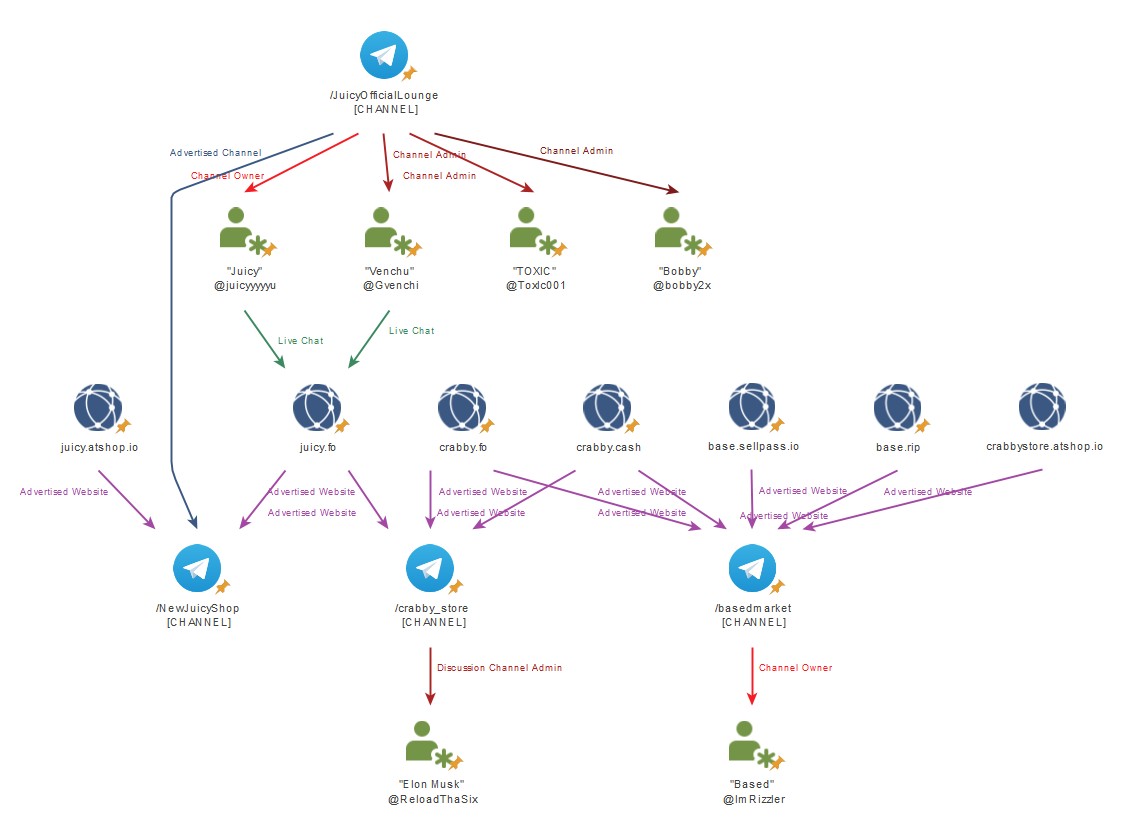
In May 2024, “Juicy” demonstrated a change in behaviour as historic messages in the /basedmarket and /crabby_store telegram channels linking the “Crabby” and “Juicy” identities together started being deleted. It is assessed this is likely due to increased pressure from Australian law enforcement. The following is clear evidence, that “Juicy” directly owns and manages the “Crabby” account store:
High fidelity evidence for attribution
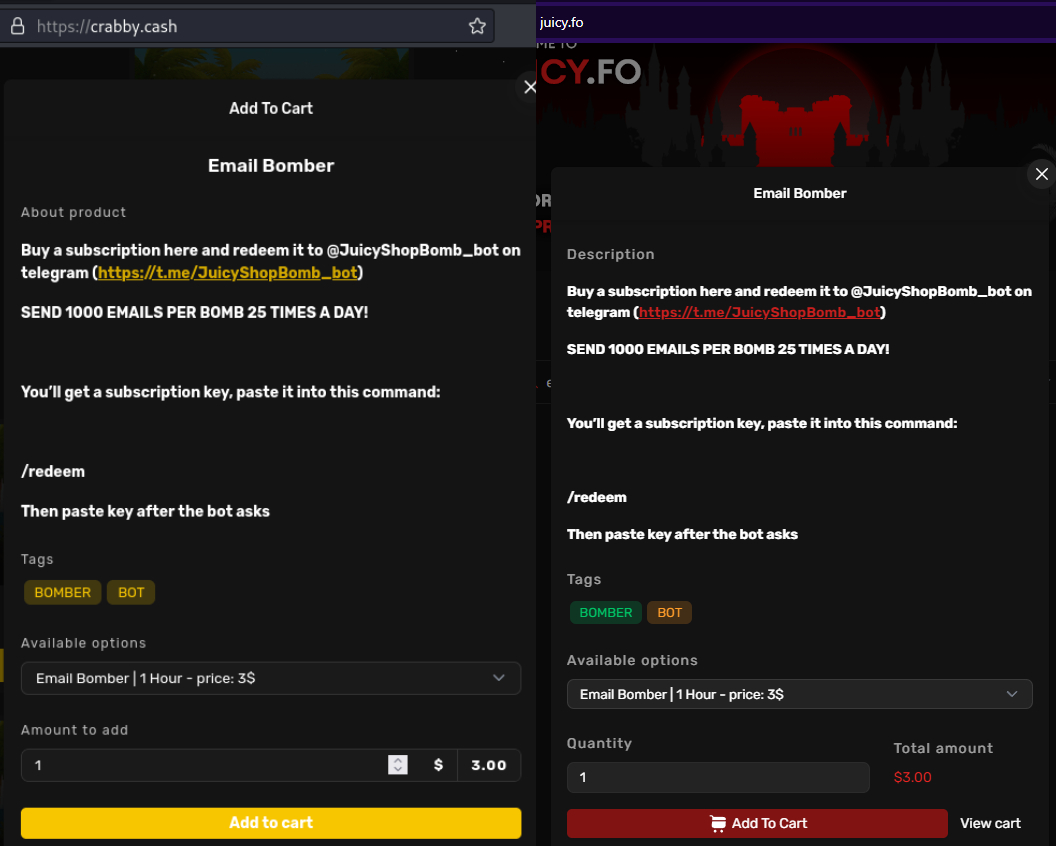
Sale of “Email Bomber”
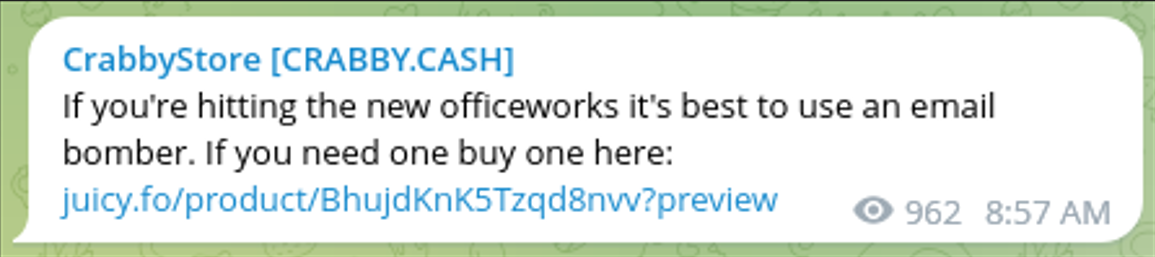
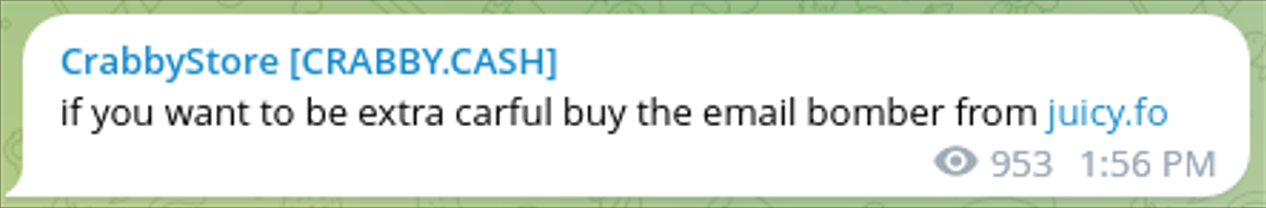
The crabby[.]cash and juicy[.]fo websites both sell the same “Email Bomber”, which links to the telegram user @JuicyShopBomb_bot. The product listing on both websites includes identical text and pricing.
Indexed telegram messages
The juicy[.]fo website has been indexed as the original chat title of the /crabby_store telegram channel, which is shown in a forwarded message in /basedmarket below. The indexed copy can be reviewed on Telemetr.
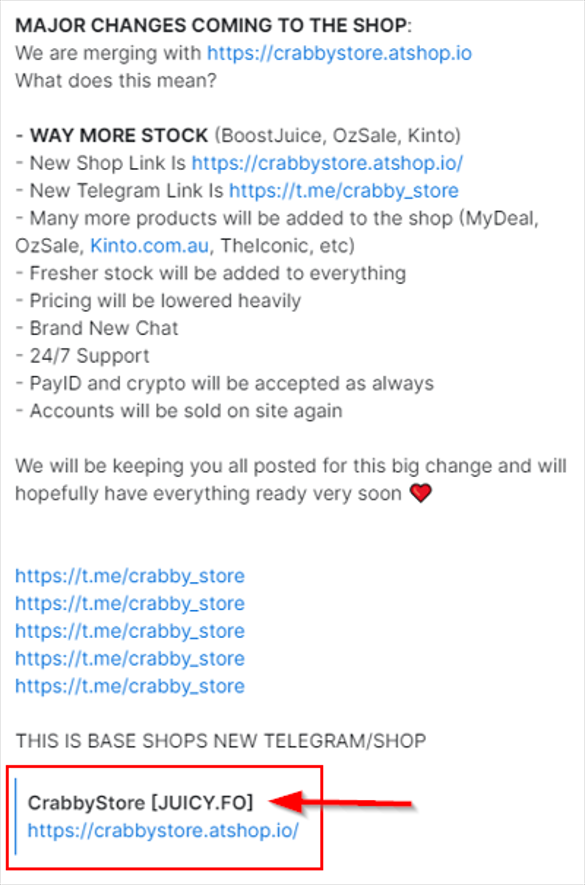
juicy[.]fo website was advertised on the /crabby_store telegram channel on multiple occasions, as shown in the images below.
Indexed terms of service
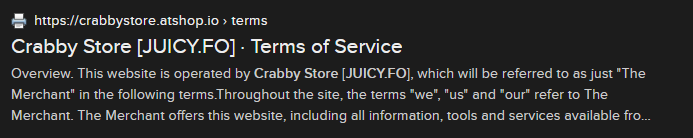
An indexed Google search of the crabbystore[.]atshop[.]io website reveals that the original terms of service included a direct reference to juicy[.]fo as the owners and operators of the Crabby store.
Low fidelity evidence for attribution
Use of atshop.io
Crabby and Juicy have both utilised subdomains on the atshop[.]io digital e-commerce website to sell their compromised accounts.
- Crabby stopped using
crabbystore[.]atshop[.]ioon 9 January 2024, and switched tocrabby[.]fo. - Juicy stopped using
juicy[.]atshop[.]ioon 20 February 2024 and switched tojuicy[.]fo.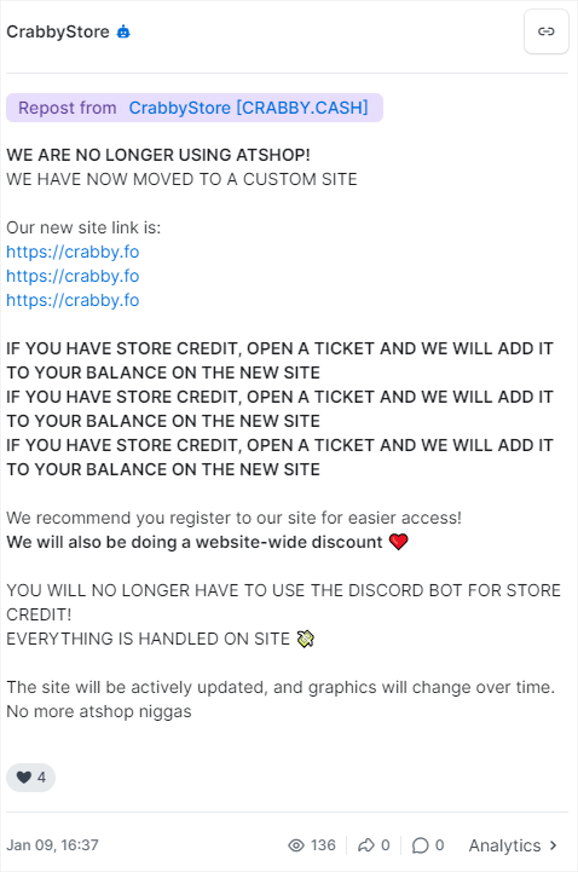
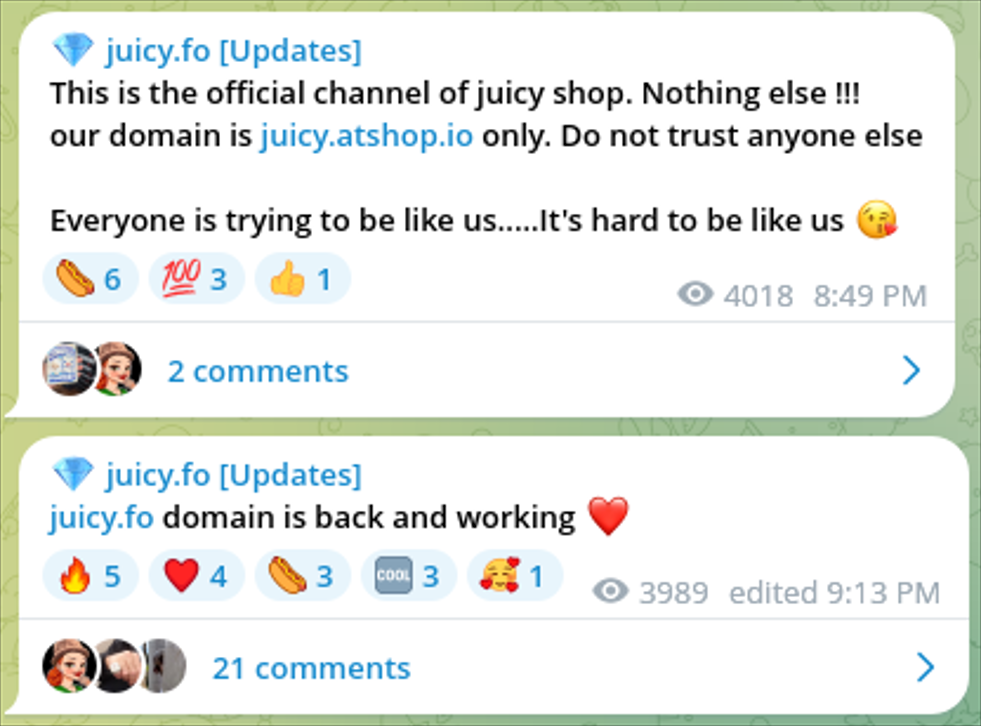
Domain TLD and registrars
Juicy and Crabby both have registered domains with the same TLD (.fo), and have used the same domain registrars. This detail is not a key indicator of attribution, but the TTPs are overlapping and should be mentioned.
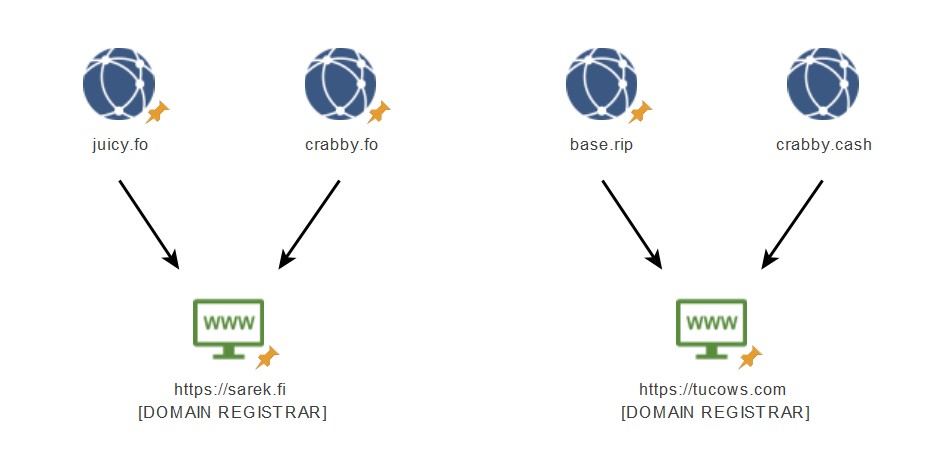
Use of privatebin.net
Crabby and Juicy both used privatebin[.]net as an online pastebin tool to freely shared compromised accounts in giveaways to Telegram users. This detail is also not a key indicator of attribution, but as there are a variety of online pastebin tools available, the TTPs are overlapping and should be mentioned.
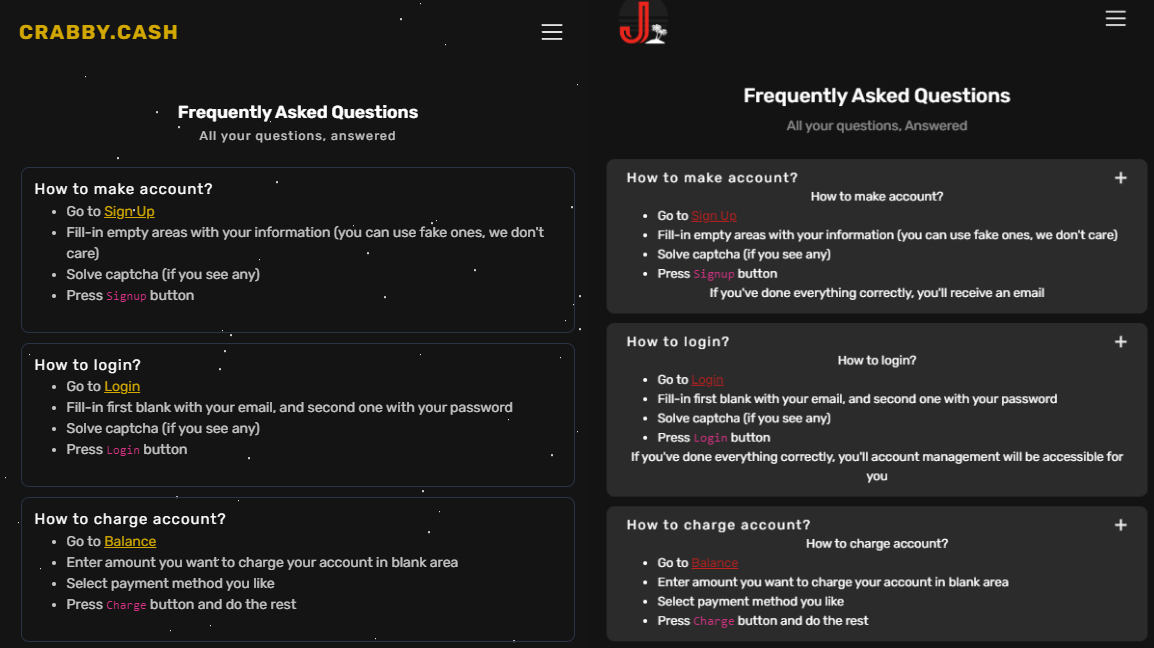
Website FAQ information
The FAQ page of Crabby and Juicy’s websites include identical questions and answers, as shown in the image below.
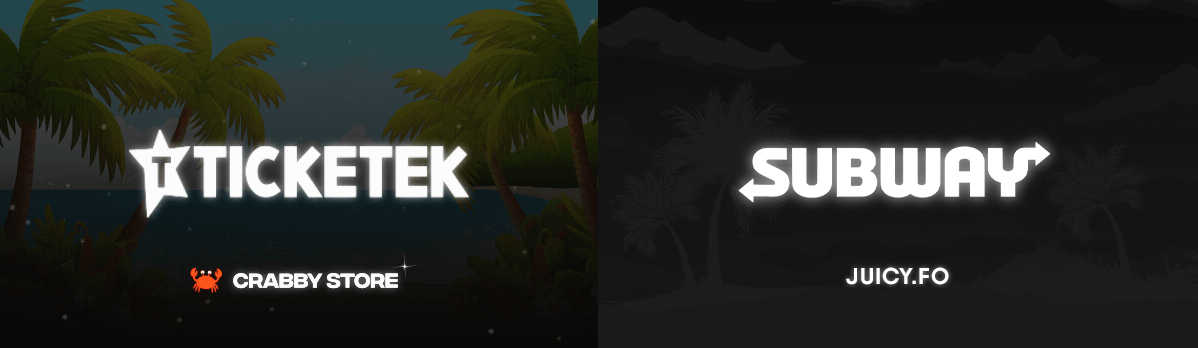
Website product images
Both Crabby and Juicy host their website product listing images on imgur.com, and include the following formatting similarities:
- 600 pixels wide by 350 pixels height
- Palm trees as background
- Affected brand logo centred
- Website name centred below affected brand name
Who is “Juicy”?
Whilst the juicy[.]fo domain was only registered on 7 August 2023, a high level of maturity and sophistication was shown indicating that the website owner has had previous experience with credential stuffing and compromised account sales.
Multiple account selling and fraud related Telegram channels were acquired and merged in the early months of the Juicy shop launch to attract new customers. These channels were likely purchased for cryptocurrency with the original owners selling their hijacked accounts in bulk for the new Juicy shop. This included:
- “Hoodupdates” was acquired on 6 August 2023, including the
/hoodupdatesTelegram channel, which now advertisesjuicy[.]fo. - “YSL” was acquired on 7 August 2023, including the
/juicystockupdatesTelegram channel (original channel name was changed), with 22,000 subscribers, to advertisejuicy[.]fo. - “Buzz” was acquired on 7 August 2023, including
buzz[.]tf,bin[.]campand the/NewJuicyShopTelegram channel (original channel name was changed), which all now redirect and advertisejuicy[.]fo. - “Legalized” was acquired on 24 August 2023, including the
/legalizedshopTelegram channel, which now advertisesjuicy[.]fo. - “Kinder” was acquired on 20 September 2023, including
kinder[.]topand the/kinderTelegram channel with 3,600 subscribers, which both now redirect and advertisejuicy[.]fo. - “TrapTop” was acquired on 13 November 2023, including the
/trapchatv6Telegram channel, which now advertisesjuicy[.]fo.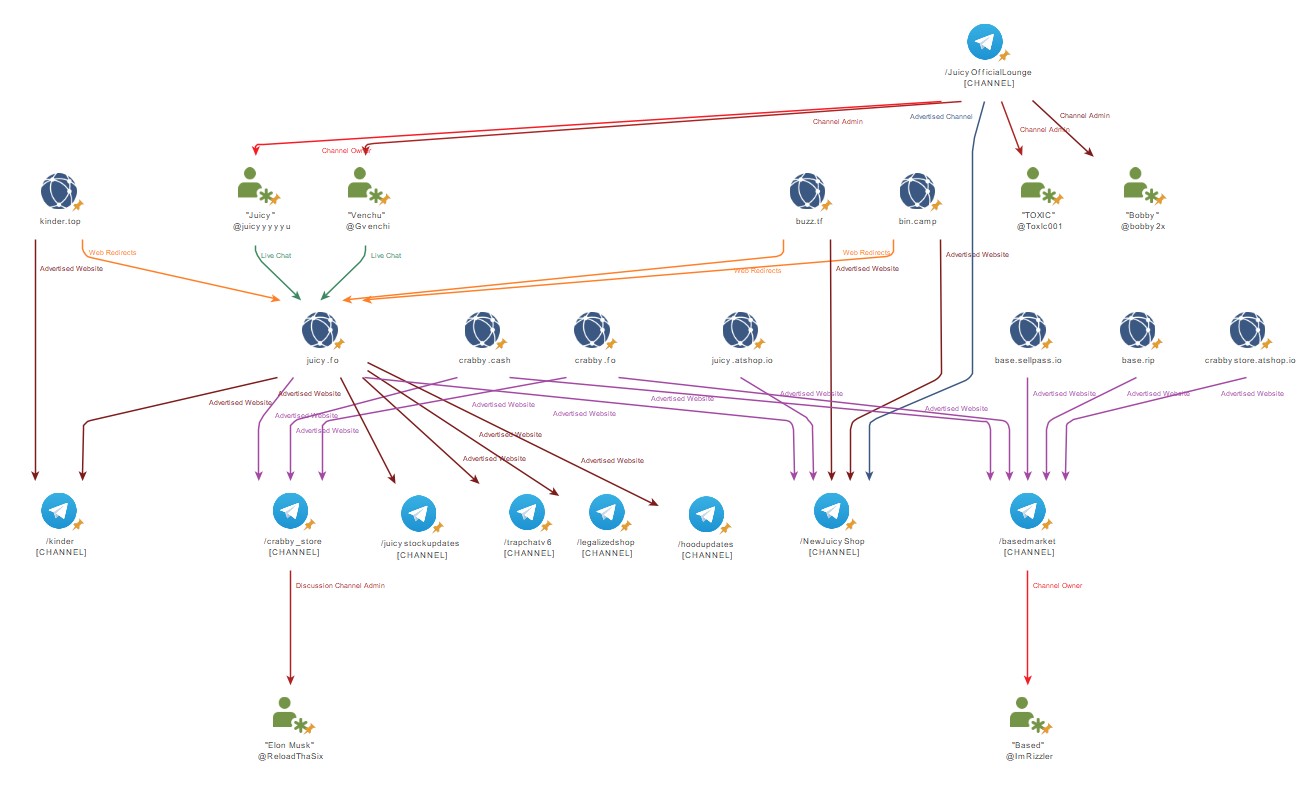
5. Who is buying the compromised accounts?
Low-level fraudsters with “boots on the ground” in Australia have been purchasing the compromised accounts from Crabby with the primary goal of monetary gain. However, these fraudsters often demonstrated poor operational security, oversharing information about the crimes they were committing.
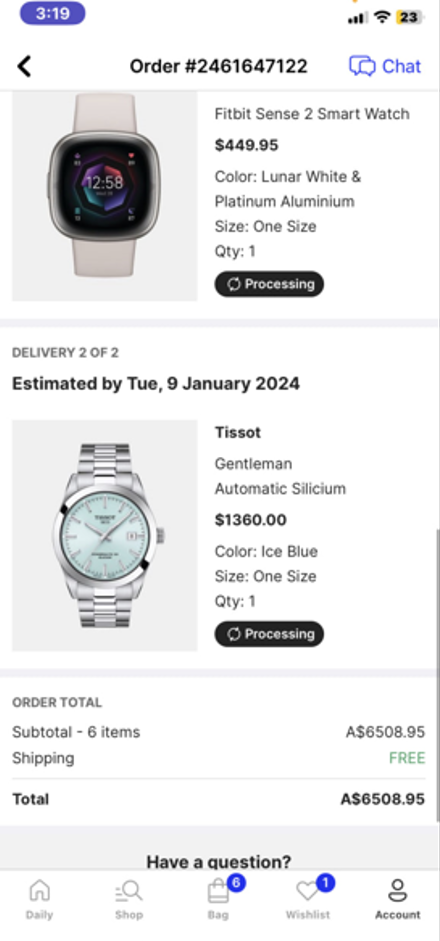
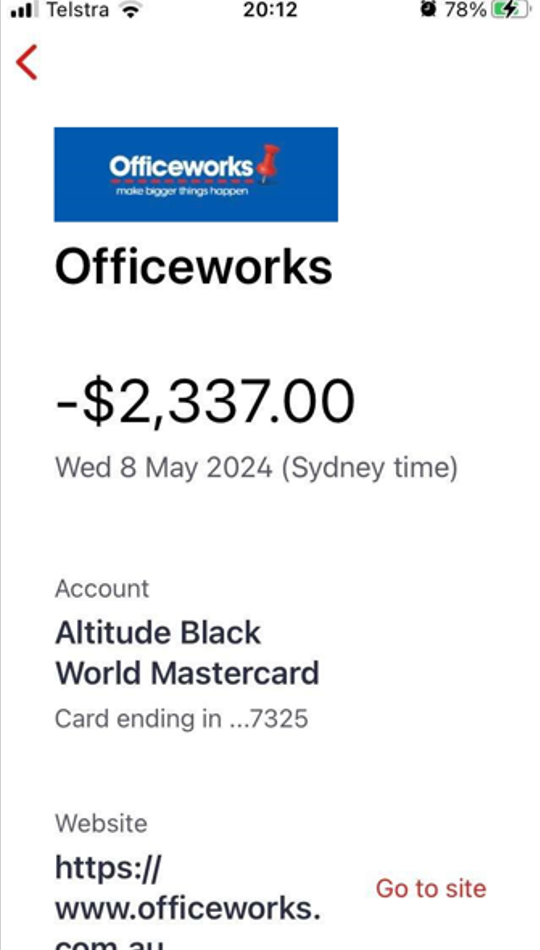
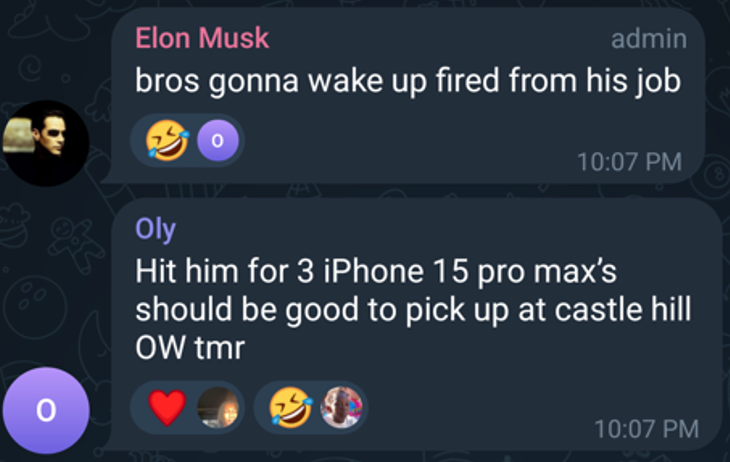
In one instance, a user called “Oly” (@jimmyweb19) shared how they used a compromised Officeworks account to place an order for an iPhone 15 Pro Max for $2,337.00 AUD, sharing the following screenshot.
“Oly” subsequently boasted to the chat about how he had called the victim, and impersonated an Officeworks employee to ask them to provide a one-time-pass code that was sent to their mobile to authorise the transaction. He shared a video using the OTP to confirm the Officeworks order, as shown below.
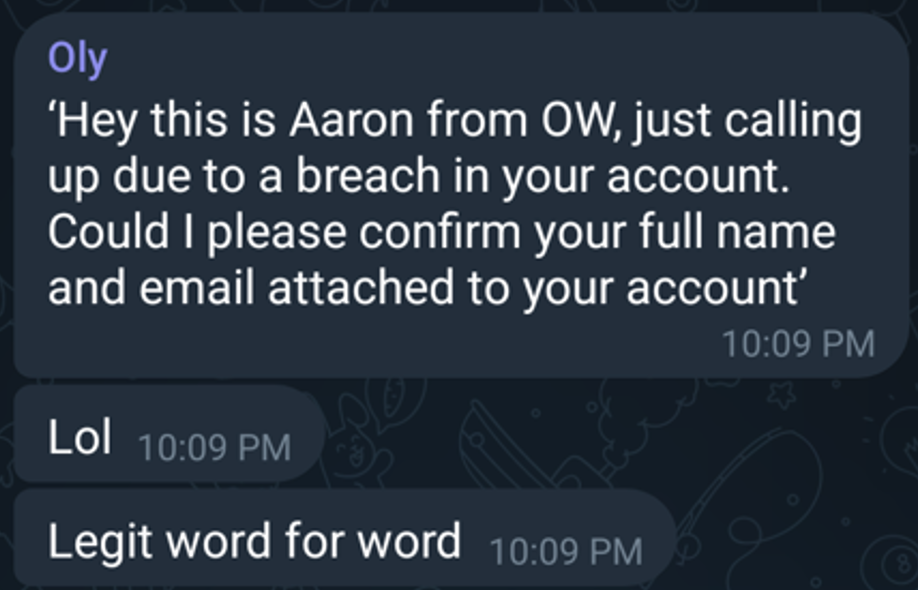
It is clear that customer of Crabby, like “Oly” are also driven by the excitement and challenge of engaging in illicit activities, and would take risks in pursuit of their goals for financial gain. The following was able to be derived about “Oly” from the information shared:
- A fraudulent Officeworks order for $2,337.00 was placed on 8th May 2024.
- Allegedly the order was for an iPhone 15 Pro Max, and he placed 2 other orders, for a total value of $7,200.
- Allegedly the items were to be collected at Castle Hill Officeworks in Sydney on 9th May 2024.
- Allegedly the orders will be picked up by “runners”, which are mules doing the dirty work.
- Victim’s card is Westpac Altitude Black World Mastercard ending in 7325.
- Victim’s mobile phone ends in 155.
- “Oly” posted a video of committing the fraudulent purchase, local time on mobile device was 9:51pm, and the video was shared on the telegram chat at 10:05pm AWST, so he could be based in Perth, Western Australia.
6. Recommendations
For users
- Change your passwords for all of your accounts so that they are unique, and do not include permutations of existing passwords.
- Sign up to a password manager to make managing your passwords easier and ensure they are unique with high complexity.
- Enable multi-factor authentication, such as Google Authenticator, for access to accounts with sensitive information, or the ability to execute financial transactions, based on your personal risk tolerance.
- Use a one-time email forwarding solution, such as DuckDuckGo Email Protection, to keep your primary email hidden.
For companies
- Implement an out-of-band notification to customers by email or mobile, when a new sign in is detected, or a privileged action is performed.
- Implement a bot mitigation solution to block traffic from automated scripts performing credential stuffing.
- Enforce minimum 14 character passwords with high complexity.
- Ensure error messages for registration, login and password recovery do not include varying responses which could enable an adversary to enumerate valid accounts.
- Enforce multi-factor authentication for accounts that transact above a specified monetary quantity, based on risk tolerance.
- Restrict access to administrative web endpoints to the organisation’s internal network IP range.
For law enforcement
- Catch and prosecute the low-level fraudsters in Australia who are buying the compromised accounts, to set a precedent and deter others from engaging in similar activities.
7. Indicators of compromise
Websites
crabby[.]cash
crabby[.]fo
crabbystore.atshop[.].io
base[.]rip
base[.]sellpass[.]io
juicy[.]fo
juicy[.]atshop[.]io
buzz[.]tf
bin[.]camp
kinder[.]top
Telegram Users
@ImRizzler | ID: 6635603118
@ReloadThaSix | ID: 6900158558
@Reloaded_6 | ID: 6900158558
@Reloaded_7 | ID: 7112193533
@juicyyyyyu | ID: 5463709914
@Gvenchi | ID: 1833637210
@pooron | ID: 6143768133
@Toxlc001 | ID: 5005608279
@bobby2x | ID: 5310517271
Telegram Channels
crabby_store
crabbychat
JuicyOfficialLounge
JuicyVouchCenter
JuicyShopBomb_bot
juicdydrop_bot
NewJuicyShop
juicystockupdates
basedmarket
basedvouches
basevouches
trapchatv6
kinder
hoodupdates
legalizedshop
Discord Invites
/WwEVuWVekT
/AN2XBYYdyq
/ZGK4vrtQ
/TQxYAbxUSE