Black Hat USA 2024: Interviews with Extorters 'Ego' and 'Reiko'
Introduction
At Black Hat USA 2024 in Las Vegas, I presented “From Doxing to Doorstep: Exposing Privacy Intrusion Techniques used by Hackers for Extortion.”
This research featured first-hand insights from individuals engaged in doxing, through exclusive interviews, which have never been disclosed to the public previously. This included a wanted threat actor involved in a DEA Data Portal hack, and an administrator of the largest doxing website, Doxbin. This provides a rare glimpse into the secretive world of doxing, and lesser-known privacy intrusion techniques, such as impersonating law enforcement and submitting fraudulent Emergency Data Requests. I will make a detailed blog post on my research into doxing and extortion at a later date.
The intention of this blog post is to share the interviews I conducted, marking their first public release.
Interviews
‘Ego’
The first interview was with ‘Ego’, a wanted threat actor from the 5-man doxing gang ‘ViLE’ in August 2023.
This gang had 2 members charged by the US Department of Homeland Security for breaching federal law enforcement databases and posing as police officers to defraud social media companies in March 2023. As per the affidavit, this was done so that ViLE could gather sensitive information on doxing targets, and use physical intimidation tactics to extort them.
The arrested ‘ViLE’ members were called ‘Weep’ and ‘Convict’. Shortly after they were charged, ‘ViLE’ released the following tribute video on their website, highlighting their compromised DEA data portal access which was used for doxing and extortion.
The frame at 0:41 of the above video, confirms that ‘Ego’ was one of the 3 surviving members of ViLE.

‘Ego’ went into hiding on 30th August 2023 shortly after the interview was completed. I suspect this is due to his regret for participating in the interview and drawing attention to himself, with a potential fear of arrest or prosecution from law enforcement.
I established initial contact with ‘Ego’ over Telegram, after finding his Telegram handle @asfhahsf in an archived page of the ViLE website.
I convinced ‘Ego’ to go on the record and complete an interview with me, as at the time ViLE had claimed journalists were falsely accusing them of being far right extremists. I referenced the following post that ‘Kt’ had made on Twitter to ‘Ego’, and offered to complete the interview from the perpsective of myself as a cyber security researcher, and not a journalist. I provided my identity and credentials, and an example of previous research that I had published.
He confirmed he would answer my questions through text, and I prepared a list of questions for him to answer all at once as per his request.
I sent ‘Ego’ two seperate batches of questions, which he responded to with links to pad.riseup.net, a temporary text sharing website.
The following image is a screenshot of Ego’s responses from the pad.riseup.net website links he sent me.
For ease of reading, I have extracted Ego’s responses to the interview questions from the pad.riseup.net links he sent me into the transcript below.
Click to view interview with 'Ego'
- When did you first become involved in doxing?
I was introduced to all of this when I was younger, through a couple of friends I knew from Xbox. They had a knack for getting hold of people’s IPs they didn’t like and had this technique called ISP Doxing. Essentially, they’d contact the internet provider and somehow manage to extract information about the person behind the IP address. Things escalated, and they even started extorting money from the individuals they targeted. That’s how this whole saga began.
- How did you find out about the Doxbin website originally?
I got my invite thanks to a friend of a friend. They were already pretty established in the community and figured I’d fit right in, knowing I was already clued in on the subject.
- You are ranked as a “Clique” user on Doxbin. What does this mean?
Clique are people who are personally friends with the owner(s).
- Did you use the darknet Doxbin site in 2011 to 2015, or only the new clearnet site founded in 2018 by Kt and Brenton?
I’ve only ever used the clearnet website, I was not familiar with doxbin or really the dark net during those earlier times.
- On the Doxbin website, it reads “It is your sole responsibility to manage and uphold your online anonymity. You are not intuitively guaranteed the right to be anonymous.” Do you agree with this quote, or have anything to add to it?
This quote really sums up the whole idea of the community. It’s on the users to keep their online security tight, but let’s be real, no matter how careful you are, someone might still track you down. Complete anonymity? Yeah, no. I’ve been there—I’ve managed to uncover big shots in the community that even the feds missed. There’s a bunch of stuff that goes into doxing, stuff most folks wouldn’t even guess, even some of the folks here.
- Doxbin explicitly disallows threats for acts of violence, however, do you believe that some users might leverage a person’s dox for intimidation or physical threats?
Yes, considering I’ve seen it happen with my own two eyes. I’ve seen people get doxed and that ending up in them being bricked, getting their house shot up, getting a molotov thrown through their windows, gang stalked, all in an attempts to extort them for money. Then there’s those who take it a step further and break into the residence, torturing these individuals with anything from cutting their fingers off to killing them, all to take the crypto currencies they behold. Things gets pretty wicked online, much more than people realize.
- You mentioned that you’ve seen violence from doxing with your own two eyes. Can you go into more details about what you’ve seen yourself? Does it all come back to money?
I’ve witnessed some pretty gruesome incidents – like people having their fingers severed, another guy getting shot in the chest, and even someone nearly losing their hand. It’s pretty wicked. There have been instances where young teenagers were subjected to days of torture before being discarded in a ditch. These acts were usually driven by the motive to acquire cryptocurrency. It’s wild to think about, but I suppose if I were face-to-face with someone holding $40 million in crypto, I might be tempted to take similar actions.
- Do doxbin members also pay for their dox targets to be bricked or intimidated physically?
Those who have the means often go for it, and some of the members even provide these services. The range of offerings is quite extensive, from bricking to resorting to firing shots at their homes from the outside.
- Do you think Doxbin has changed for better or worse as it has become much more popular in recent years?
Depends on who you ask, coming from someone who’s been involved for a majority of it, it’s softened up a bit for sure. There used to be a strict policy that anything uploaded stays uploaded, no excuses. However the clearnet website started off by offering to remove pastes for money, which well, earned well above 6 figures yearly. However towards the end, the owners wanted to honor the old code, and eventually stopped removing pastes for money. It’s all a matter of perspective. From my vantage point as someone who’s been deeply immersed in it, I can say that things have definitely mellowed out to some extent over time. There was a time when a stringent rule prevailed: once something was uploaded, it stayed there, no exceptions. But then the clearnet website introduced a new twist by offering to take down pastes in exchange for money. And well, that turned into quite the lucrative enterprise, raking in well over six figures annually. However, as things drew to a close, the original principles started to hold more weight again. The site owners decided to honor the old code and eventually ceased the practice of removing pastes for payment.
- You mentioned that doing private doxing services can generated up to a six figure income. Do you do this full time, or are you studying/working a day job outside of this?
I’m relatively young, I’d say. I’ve never experienced the typical 9-5 work routine, and honestly, I don’t see that changing. My focus has been on studying networking, and I recently graduated with a degree in networking engineering. Along the way, I managed to pick up a few different network certifications. While I was studying, this has pretty much been my gig for the past year.
- What type of people do you perform doxing on?
Anyone, as long as there’s someone there to pay me for it.
- Do you have a preference for those that have committed wrongful acts, such as paedophilia, animal abuse or scamming?
I generally don’t target individuals unless it’s for personal motives or in collaboration with my group. However, I did make an exception once. A young woman in my community confided in me, sharing a disturbing story about a guy who was part of the community back then. He had deceived her into meeting him at his apartment, where he ended up sexually assaulting her. This issue hits close to home for me because my own girlfriend went through a similar ordeal, but in this case, justice was served. You can find the details in the paste at https://doxbin.net/user/ego — it’s the only paste I have up there. Everything is explained in deep detail. It’s a fun read.
- You mentioned you have a girlfriend, does she or anyone else in your family know about the activities you complete online?
I don’t have a big family to discuss this with, so there’s no one to weigh in on it. The only person who really knows about my endeavors is my girlfriend, and even then, she barely knows anything.
- Do you ever find yourself in an ethical dilemma, have their ever been circumstances where you decided not to publish a dox?
Living with schizophrenia has made me rather emotionally detached. I don’t experience much remorse or empathy toward others, which strangely aligns well with the nature of the work I’m involved in.
- What is your intention when posting an individuals’ information on Doxbin?
My name was only associated with pastes when working with our group, and these instances were intended to draw attention to both the community and law enforcement in specific situations. We were well aware of being under surveillance by the authorities so that wasn’t difficult.
- You mentioned that you have posted doxes whilst being well aware that you are under the surveillance of authorities. How does this make you feel, are you ever concerned that you could also be apprehended by the authorities?
I’m not really bothered by it. If they’re determined to track me down, they’ll manage to do so. I’m realistic about the fact that if the US government is genuinely interested in locating me, they have the resources to do it. By the way, I’ve flown into the US multiple times since I started this, and I’ve had no issues whatsoever.
- Are you ever concerned about someone posting your dox online?
No not really. No one has even come close. Even my close friends with extensive experience couldn’t dig up anything substantial. All people really know about me is the name, age, and country I’ve put out there, and none of those details can be verified.
- Do you ever take down a dox, and under what circumstances?
If I were to paste something, it would stay til the end of the website. No circumstances.
- Do you rely on leveraging only publicly accessible information to complete your doxes?
As you become more acquainted with the subject, you develop the skills to uncover information that isn’t readily accessible to the public. So, no.
- Do you ever attempt to use private sources to enrich your data for doxes? (for example, private databases, socially engineering customer service, fraudulent emergency data requests)
Yes, nearly every time. I’ve taught loads of people to do the same.
- What was your initial reaction when Doxbin was sold to ‘white’ originally?
Within the first 2 weeks or so, White had given his personal number out to another individual within the community. Which well, tells you enough.
- What was the fallout and recovery like after Doxbin was returned to ‘kt’ and ‘brenton’?
Under KT’s ownership, the website consistently upheld its reputation. However, when it changed hands and was sold, its standing began to decline steadily. Fortunately, with its subsequent repurchase, the website’s reputation started to improve once again.
- Were you involved in the doxing of white?
Yes.
- Do you believe that law enforcement benefited or leveraged the dox that ‘ViLE’ did of ‘white’ for his apprehension?
Yes, the UK law enforcement has publicly admitted to this.
- ‘White’ who was part of ‘LAPSUS$’, was involved in some very large breaches. Is this kind of activity common amongst your peers?
Many of my friends are involved in very similar activities on the daily.
- How do you feel about ‘kt’ and ‘brenton’ stepping down as administrators most recently, and handing over the site to ‘Operator’?
It’s about time for them to step down and move on. This has been their project for the past 5 years, and has been built from the ground to where it stands today.
- Do you trust ‘Operator’, and do you feel there is any risk that ‘Operator’ could jeopardize Doxbin as ‘White’ previously did?
I don’t trust anyone, but in this situation, I suppose I can give him the benefit of the doubt. Whatever he chooses to do won’t affect me one way or another. I did some research on him when he first appeared, and it wasn’t hard to uncover what he does and has been up to before doxbin. So, based on what I know, yeah, I can confidently say he’s trustworthy.
- How do you feel about the recent arrests of two ViLE members?
It’s indeed disheartening to witness the situation unfold, seeing two friends facing legal consequences. Regardless of the circumstances that led to their situation, it’s tough to observe. The ripple effect on other group members adds to the difficulty. On a more positive note, I’ve maintained contact with both of them, and it’s reassuring to know that they’re staying strong. Wishing them all the best as they navigate through this challenging time.
- Did you know they had made unauthorised access to the DEA web portal?
No comment.
- What prompted you to end ViLE?
With the recent legal issues affecting two of our members and the impending sale of doxbin, we’ve collectively reached the decision to bring our journey to an end.
- What do you have to say about the US Attorney Office describing the members of ViLE as those who shame, intimidate and extort others online?
It’s no revelation that people often bend the truth to present themselves in a more favourable light. This is a widely acknowledged reality.
- Are there any major misconceptions that journalists have made about the members of ViLE or it’s purpose?
Absolutely, it’s quite common to come across articles that are riddled with falsehoods and lack any substantial evidence. Unfortunately, some resort to such tactics to generate a few more clicks, which is indeed a disappointing and unethical. This behavior is widely recognized and acknowledged within the industry.
- You mentioned that journalistic articles are riddles with falsehoods. Could you describe what these are?
When I mentioned journalistic articles containing falsehoods, I was referring to instances where media outlets inaccurately label individuals or groups, branding them as criminals or such without substantial evidence. These kinds of mischaracterizations can be damaging and misleading, as they can distort public perception and perpetuate stereotypes. It’s important for journalists to exercise diligence in their reporting, ensuring that claims are supported by credible sources and thoroughly fact-checked to maintain the integrity and accuracy of their work. But hey, that’ll never happen.
- What are the common mistakes you see people make that lead them to get doxed?
Individuals consistently employs identical email addresses across all their online accounts, along with reusing similar passwords for each one. They also opt for consistent or similar usernames across various platforms. They choose not to use VPNs. Moreover, they openly share their complete names and general location on social media platforms. To add to this, they freely post personal pictures, potentially compromising their own privacy and security.
- What would you recommend to the general public to protect themselves against doxing?
Don’t do anything listed above.
‘Reiko’
The second interview was with ‘Reiko’, an administrator for the doxing website ‘Doxbin’, in September 2023.
Doxbin is the largest doxing community online and has amassed over 300,000 users and 165,000 published doxes. ‘Reiko’ stepped in as a new system administrator and developer for Doxbin, after the website was sold to ‘Operator’ in June 2023. It was sold by the original founder ‘Kt’ who was also a member of ‘ViLE’, after he went into hiding when the other group members were charged.
‘Reiko’ dissappeared in May 2024, after the new owner of Doxbin ‘Operator’ had been kidnapped. This was shortly after ‘Operator’ had his own dox posted by a rival gang to the Doxbin website, and subsequently videos emerged of his kidnapping and extortion for $400,000 USD in Monero. Due to the close association ‘Reiko’ had with ‘Operator’, he quickly disappeared after those videos came to light.
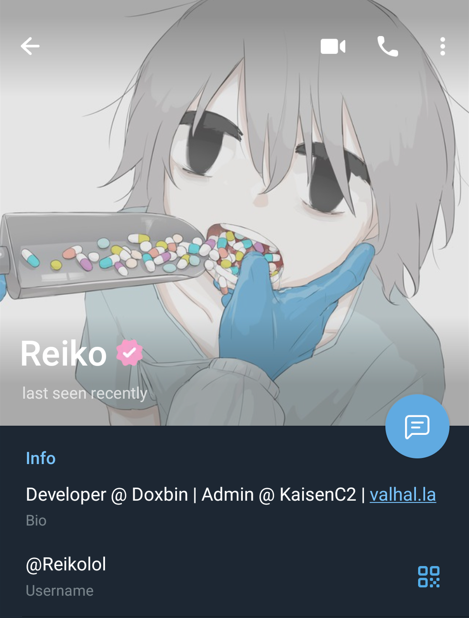
I established contact with ‘Reiko’ over Telegram. His telegram handle @reikolol was accessible in many locations, such as the doxb.in website, as a ranked channel member on the Telegram channels t.me/doxbin and t.me/pastebin, on his Doxbin profile, and on his personal website reiko.gay.
I invited ‘Reiko’ to speak to me, and shared that I had recently completed an interview with ‘Ego’.
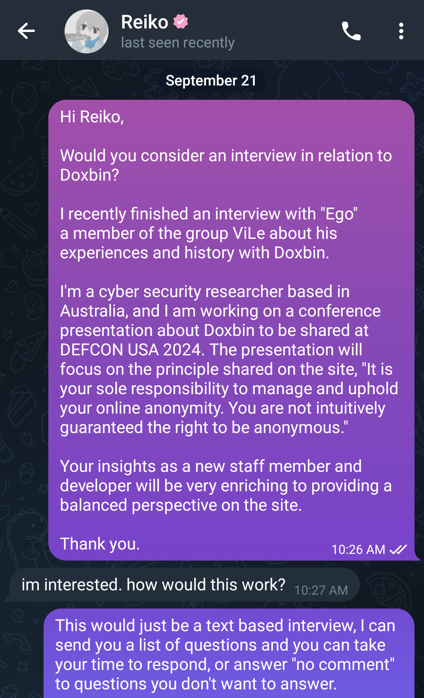
He was happy to proceed with a text-based interview.
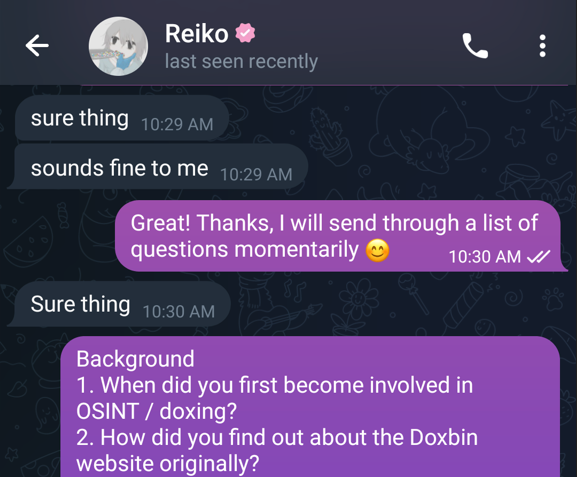
I structured this interview the same as the one with ‘Ego’, whereby I sent a list of questions in bulk for him to answer and provide back to me.
For ease of reading, I have extracted Reiko’s responses to the interview and included them in the transcript below.
Click to view interview with 'Reiko'
- When did you first become involved in thing?
I became involved with doxing in 2016. I was originally introduced to it on a social platform in which I wanted to expand on my cyber security knowledge and then had involved myself with a community of people who had gotten me to learn OSINT. Sadly, the community was not a good one, to say the least.
- You mentioned that the community that introduced you to Doxing was not a good one. Can you elaborate further on this? Was it not good because of the sophistication of the members of the group, or because their objectives were ill-informed?
Well, I was a minor at the time and had come to find out that the group I had been involved with were swatting underage females behind my back for absolutely no reason. When I had found out, I immediately cut contact with those people and also destroyed any reputation the members had. I cannot comment on what the group was, sadly.
- How did you find out about the Doxbin website originally?
Originally, I had a friend group a few years back who had talked about the website. My OSINT ‘skills’ were not as advanced back then and upon being introduced to the website by some friends, I had skimmed over a few ‘pastes’.
- How did you become a developer or system administrator for Doxbin?
Initially, I had found a solution within Doxbin that prevented users from being able to see their profile picture. I had contacted Operator explaining the solution and then we worked on it together. After this, I continued to help out development wise with features, changes and fixes towards the site until I was essentially labelled the Developer of Doxbin.
- Do you have previous experience running similar sites?
I do not. Doxbin is the first of its kind for me.
- Have you had experience with the development of any other websites or personal projects prior to working on Doxbin? (Even if not related to doxing).
Yes. I used to be a leader alongside another individual for a group called Valhalla. The website for this group was quite popular and ViLE had even taken inspiration from the website. That is one of the ones I can remember. As for personal projects, I sometimes just get bored and work on a project and then don’t usually finish it. One of them was an anime site I was working on that I simply just left.
- How do you ensure anonymity and operational security when setting up and maintain infrastructure? Do you rely on bulletproof hosting?
If you mean anonymity for Doxbin and our users, we do not store IPs and we do not store any personal information. Here is an example of what we only store: [21/Sep/2023:01:34:06 +0000] “GET / HTTP/1.1” 200 664 “https://doxbin.com/" “Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.3) Gecko/20100401 Firefox/3.6.3” This is also wiped from our servers after 7 days. As for bulletproof hosting, it is not necessary. Doxbin is not illegal. This is due to Section 230 of the Communications Decency Act.
- Regarding security considerations when administering Doxbin, the original question was more so in terms of infrastructure maintenance. For example, do you utilise a jump host to pivot to via from your home network, before accessing backend Doxbin infrastructure?
We have jump servers and firewalls. We also have reverse proxies and so on. We also have a hosting control panel to make things easier for everyone. I cannot state anything else, sadly.
- To maintain your own anonymity and prevent doxing, do you utilise any counter-intelligence methods?
I used to pretend to be from somewhere I wasn’t when dealing with a situation that involved annoying people in a situation with a company owner. I cannot expand on that sadly. The company owner and associates believed I was in an Asian country since I presented a false time zone on my system, posted an uber eats screenshot that was in a completely different country and so on. Nowadays, people just know where I’m from.
- On the Doxbin website, it reads “It is your sole responsibility to manage and uphold your online anonymity. You are not intuitively guaranteed the right to be anonymous.” Do you agree with this quote, or have anything to add to it?
I heavily agree with this quote. It is your responsibility to uphold your privacy on the internet. Have you ever been told in a school assembly about the dangers of the internet? Even schools teach children about being private on the internet. Why is something that is taught to people in schools that is very important and should be taken seriously, not utilized? In short, this quote is very true.
- What type of people do you perform OSINT or Doxing on?
I utilize OSINT mainly on pedophiles. This is due to the fact that I dislike pedophilia with a passion.
- Do you have a preference for those that have committed wrongful acts, such as paedophilia, animal abuse or scamming?
I do, indeed. Let us take Courtney as an example. She is a 26 year old female who had engaged in sexual acts with 14-17 year old boys and mentally scarring them (possibly for life). I believe such a person should not be allowed to hide. The same goes with animal abusers and rapists. Those are the main types of people I dislike and will go out of my way to ‘paste’.
- Do you ever find yourself in an ethical dilemma, have their ever been circumstances where you decided not to publish a dox?
Yes, I have had some dilemma’s. I had been working on a pedophile case that the police could not do much about due to how the evidence was obtained. I had collected all the information but was not able to publish the ‘paste’ due to the fact that the pedophile could have also endangered his victims. However, I was able to figure out a solution which I cannot state and thus, the predator was put in prison and ‘pasted’.
- You talk about an ethical dilemma about posting a dox related to a paedophile case, due to how the evidence was obtained. In my discussion with Ego, he mentioned that he would often use private sources (e.g. RATing a target’s device, social engineering customer service, fraudulent emergency data requests) to enrich his pastes with more detailed information. Are you referring to similar in this case, could you elaborate?
The information was obtained through allowing me to gain access to an account through commonly used passwords. This is technically a form of hacking which would mean the evidence I present would be obsolete in a court of law and I could also get charged.
- Doxbin explicitly disallows threats for acts of violence, however do you believe that some users might leverage a person’s dox for intimidation or physical threats?
Doxbin does not allow for internal threats within our website. Whatever happens outside of doxbin is not our responsibility. Think of Doxbin as a whitepages alternative. You can search for a user that has been ‘pasted’ on our website and if the person is on our website, the results will show. The same can be applied for a whitepages search. If Doxbin must be criticized for allowing users to share such information, why should these same people who criticize Doxbin so much, not also criticize online directory services?
- There has been some videos shared in Doxbin telegram channels featuring acts such as shooting guns outside of target’s homes, and throwing bricks through their windows. Do you have any interesting stories you could share from your experience with users on Doxbin?
Sure. There’s a few instances where online situations can turn into physical matters in real life. An example of this is a person called ‘Mike Virus’. He had been jumped by a group of people which I will send you the video of. The reason why he was jumped was because of the countless attempts of harassment he had done to random people online.
- Many Doxbin pastes include commentary such as “Please go through with your suicide” and “Do your worst on them”. Would you consider this threats of violence? How do you determine when/if it’s okay to make similar statements?
I wouldn’t consider this threats of violence. At the end of the day, all it is, is an additional number to the over 120,000+ pastes on Doxbin. Nobody would “do their worst”. As for the suicide stuff. I wouldn’t say it’s a threat of violence at all. Technically, nobody is being threatened. An example of this is in my ‘paste’ on Courtney where I stated the following: “Oh! And as a final note to Courtney. Stop threatening people with your suicide. Nobody would truly miss you if you decide to do it. Not your mother, your sister, your friends, your relatives or anyone remotely close to you. Please go through with it.” This is not a threat of violence as nobody has been threatened. As for similar statements, there’s a huge difference between “I’m going to murder you” and “You should kill yourself”.
- How does the Doxbin team decide whether or not a paste is added to the ‘Hall of Autism’?
Well, to add someone to the hall of autism, you must pay for it. The team also has other considerations they must take towards allowing the person to be on the Hall of Autism but that usually just depends. You can’t just put someone on the hall of autism for absolutely no reason just because you have the money.
- What are the common mistakes you see people make that lead them to get doxed?
Their OPSEC. People are always vulnerable no matter what. An example of this could be: utilizing the same username for a service, stating personal information, showing their face, posting a picture of where they are at. The person willingly releasing this information increases their chances of having any information found out about them.
- What would you recommend to the general public to protect themselves against doxing?
I would recommend not utilizing the same email for every service, not utilizing common passwords, not having the same username for each platform and also just having common sense. If you have to think twice about something you are going to share, post or do, it’s probably not best to do it.
- Are you ever concerned about someone posting your dox online?
Not really. Being doxed is not a concern for me simply due to the measures I have taken in place not to get doxed and if I do get doxed.
- There has been historic fallout for Doxbin when ownership changed hands, for example when White was the temporary owner in 2022. How do you feel about KT and Brenton stepping down, and Operator taking over as the new owner?
I believe that Operator has the skillset to make the platform better for our users. When I heard the news about KT and Brenton stepping down, I did know it was going to happen one day and that I knew the site would be in good hans as KT and Brenton would take more precaution than they did last time in exchanging ownership to a new Admin.
- How do you believe KT and Brenton could trust Operator in taking over ownership of the site?
Operator has the skills and the ability to allow for Doxbin to become a better platform. I believe KT and Brenton must have seen the potential in Operator and how he would manage Doxbin. In short: KT and Brenton trusted Operator and that trust was efficient enough, as we can see.
- There is rumours that Operator is a member of an initial access broker group who are notorious for social engineering and sim swapping. Do you believe that Operator has experience in this domain?
No comment.
- Did Operator purchase Doxbin from KT and Brenton? Do you know how much the site was sold for, or if there was any agreement with conditions for the sale?
Operator did purchase Doxbin from KT and Brenton. I do know how much the site was sold for but I don’t believe I am able to state that. I’m not too sure of the conditions but I can bet you one of them was to simply just make sure the site is maintained.
- When KT administered the site, he would intentionally leave files around for honeypot purposes (e.g. doxbin.org/.env). Do you intend to continue doing the same?
Fuck yes. on doxbin.org/.env, it was an extremely funny thing KT left behind and I would like to continue to leave behind little easter eggs and so on to the site mainly just because it’s funny.
- What are some of the most prolific or infamous doxes on Doxbin from your perspective?
I would have to say some doxes made by ViLE. An example of these are:
- ‘Conreppin’ - A person who claimed to be in Lizard Squad and scammed KT for $1,000. I knew this individual. He passed away and was found to have been dating 14-16 year old girls while he was 24.
- ‘764’ - A group known for extortion. Mainly to little girls.
- ‘White’ - The person who bought Doxbin originally and then ruined the site. He was then doxed and it was a very nice and detailed paste. There is more but I would say those are some of the more infamous.
- Finally, if you had anything you could share to the public about yourself or Doxbin, what would it be?
Uh. Let’s see. Here’s a piece of advice: Take your security seriously. In this modern era, no matter how safe you think you are, there is always a vulnerability to be exploited. That vulnerability is often humans. Limit who you trust and stay safe. Have a good day.